AUTHOR: Samuel Hinson, Drummond Leader for Cybersecurity Services
Penetration testing (also known as pentesting) and vulnerability scanning share many similarities, often resulting in IT professionals being unsure of which service they truly need in order to create a holistic and vigorous cybersecurity framework. This blog will provide you with the information you need to better understand the differences between each service, learn the benefits of each, and help you decide which service your organization needs.
What is a vulnerability scan?
A vulnerability scan typically consists of an automated software-driven check for known vulnerabilities in applications, systems, and networks. It can also evaluate weaknesses in user access rights and configurations that could lead to breaches. Because this scan is automated, it is generally very fast, and it is often used as part of the initial security assessment process. Vulnerability scans should be audited by an IT team to identify false positives and identify weaknesses to be addressed.
What is a penetration test?
A pentest, on the other hand, is much more comprehensive and tailored to your organization’s needs. It employs tools such as port scans and fuzzing methods to probe deeply into system architecture. Penetration testing professionals will use their knowledge and skillset to attempt various techniques—from social engineering to application exploitation—that are often employed by malicious actors to gain unauthorized access or disrupt operations. Penetration testing gives you an accurate assessment of your security posture and helps you identify any potential gaps or weaknesses.
What is the difference?
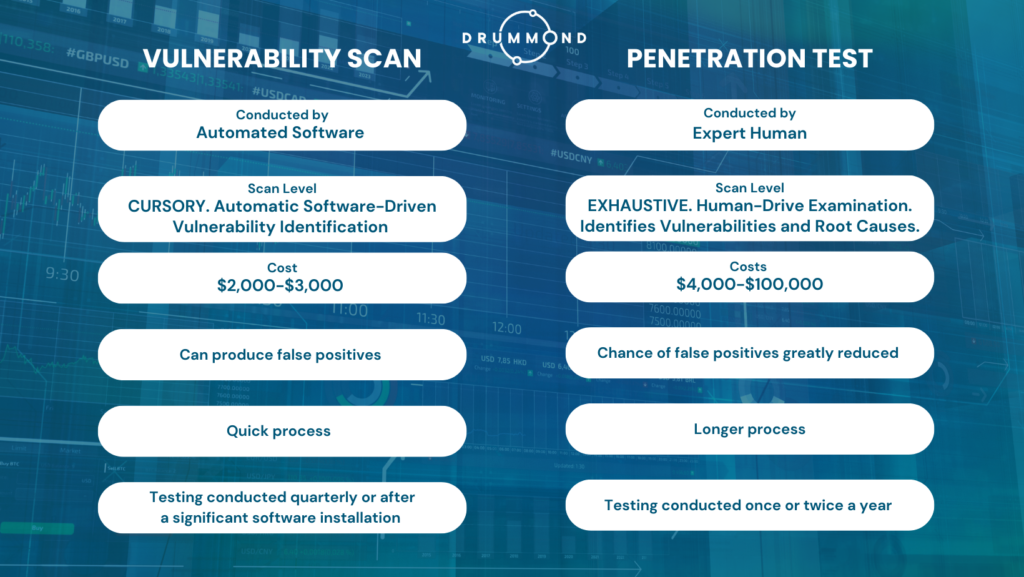
| Vulnerability Scanning | Penetration Testing |
| Conducted by an automated software program. | Conducted by an expert human. |
| High-level scan to identify vulnerabilities | Exhaustive examination to find root cause of vulnerabilities |
| Costs $2,000-$3,000 | Costs range between $4,000 for a small, non-complex organization to more than $100,000 for a large, complex organization. |
| At times produces false positives (an incorrect alert that a vulnerability is present). | The chance of false positives is greatly reduced |
| Very quick process. | The process is more comprehensive and therefore takes longer. |
| Testing should be conducted quarterly or after a significant software installation. | Testing should be conducted once or twice a year or after a significant security breach is detected and resolved. |
Which one do I need?
The quick answer is ‘both’. Both tests play a significant role in strengthening your cybersecurity. When you combine regular vulnerability scans with semi-annual or annual penetration tests, your team is armed with the details they need to shore up your organization’s defenses.
New and small organizations may be able to get by with vulnerability scans to start. While well-established large organizations should consider both and at a minimum should conduct regular penetration testing. When organizations choose a third-party assessor, like Drummond Group, they can be assured the evaluation is thorough and unbiased and that they’ll receive expert recommendations to help their internal teams prioritize. Don’t forget, mandates set forth by PCI DSS, FFIEC, and GLBA may impact your organization and dictate which type of test your organization should conduct to maintain compliance.
Ultimately, both vulnerability scanning and penetration testing are important components for maintaining a secure infrastructure. Vulnerability scans can provide quick feedback on the state of your system’s security, while penetration tests offer a comprehensive way to detect vulnerabilities that automated scans may miss. By investing in both, you can ensure your systems are better protected against malicious attacks.
Book your FREE consultation today! Reserve your spot on our free consultation calendar (spots are limited). We’ve identified the topics our customers ask about most and are ready to share our expertise with you. Topics include:
- 2FA Requirements
- Security Requirements
- Audit Logging Requirements
- Maintaining Continuous Compliance
Please note: Our consultation meetings are not sales or discovery sessions. If you’re ready to speak with a sales representative about our Cybersecurity services, please contact us.
